Secure Your System with Complete VAPT Services
Partner with us to proactively protect your business integrity and customer trust.
Why choose VAPT?
VAPT ensures proactive security by identifying and fixing vulnerabilities .
Ready for VAPT assessment?
Our team is prepared to assess and protect your systems against threats.
Top VAPT Services Provider in India
As a leading VAPT (Vulnerability Assessment and Penetration Testing) provider in India, we stand out with our commitment to thorough security assessments. Our expert team employs unique tools and methodologies to identify and mitigate potential vulnerabilities across various digital platforms. We offer complete reports and actionable recommendations customized to strengthen your security against cyber threats.
Navigating the VAPT Process
Navigating through our VAPT (Vulnerability Assessment and Penetration Testing) process ensures powerful cybersecurity for your organization. Our structured approach ensures complete protection, empowering your business to manage and strengthen its cybersecurity posture proactively. Throughout the process, we provide support and guidance to strengthen your security. Trust our systematic approach to protect your systems against cyber threats.

1. Scope
Clearly defining the scope of assessment, including systems, applications, and networks to be tested.

2. Vulnerability Assessment
Automated and manual scans are conducted to identify vulnerabilities, such as outdated software.

3. Penetration Testing
Reduce attacks to exploit identified vulnerabilities and assess their impact.

4. Analysis
Review findings to prioritize vulnerabilities based on severity and potential business impact.

5. Reporting
Compiling detailed reports that outline identified vulnerabilities, risks, and recommended remediation.

6. Solutions
Collaborating with stakeholders to implement and validate fixes, ensures systems are secure.
SUPPORT
If you have any further questions about our services, you book an appointment to speak with one of our representatives.
+91- 98118 52101
Vulnerability Assessment Audit Services
At Techchef Group, we bring over 20 years of expertise in cybersecurity to offer comprehensive Vulnerability Assessment and Penetration Testing (VAPT) services. Our Vulnerability Assessment Audit Services are designed to help you identify and address potential security weaknesses in your systems before they can be exploited. We believe in a proactive approach to cybersecurity, ensuring that your business stays protected against evolving threats.
Our team of experienced security professionals conducts in-depth assessments, providing clear insights into vulnerabilities and practical recommendations to strengthen your defenses. With a personalized approach, we work closely with you to understand your specific needs and tailor our solutions, so you can focus on growing your business with peace of mind, knowing your systems are secure. Let's work together to protect what matters most to you!
Penetration Testing Audit Services
Our Penetration Testing Audit Services provide a thorough evaluation of your security systems, helping you identify vulnerabilities before they can be exploited. With over 20 years of experience in Cyber Security, we use industry-leading tools and techniques to simulate real-world attacks, ensuring your organization is protected against both known and emerging threats.
We understand how important your business is to you, which is why our team of experts works closely with you, offering personalized solutions tailored to your unique security needs. Whether you're looking to safeguard your data, comply with regulations, or simply stay ahead of potential risks, our VAPT (Vulnerability Assessment and Penetration Testing) services give you the confidence that your security is in trusted hands. Let's work together to keep your systems secure and your business running smoothly.
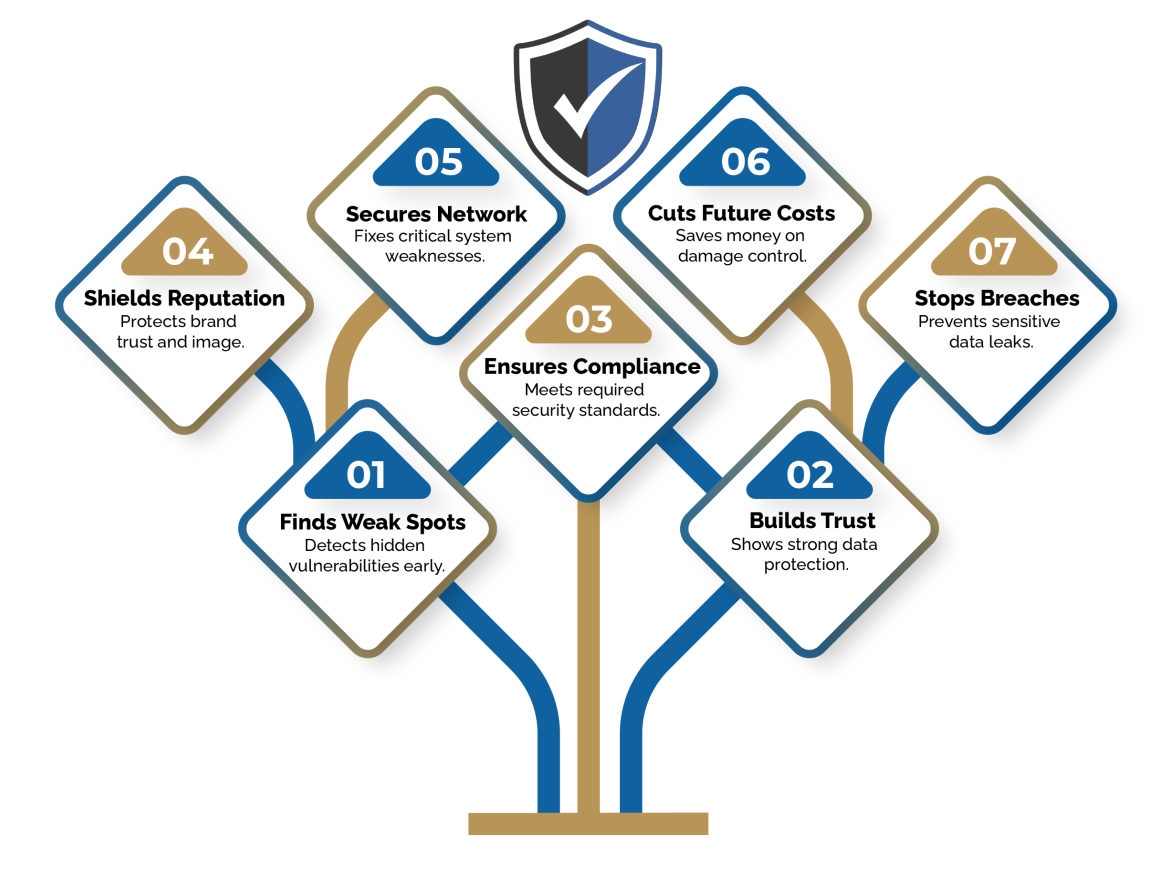
Top VAPT Advantages to Protect Your Digital Assets
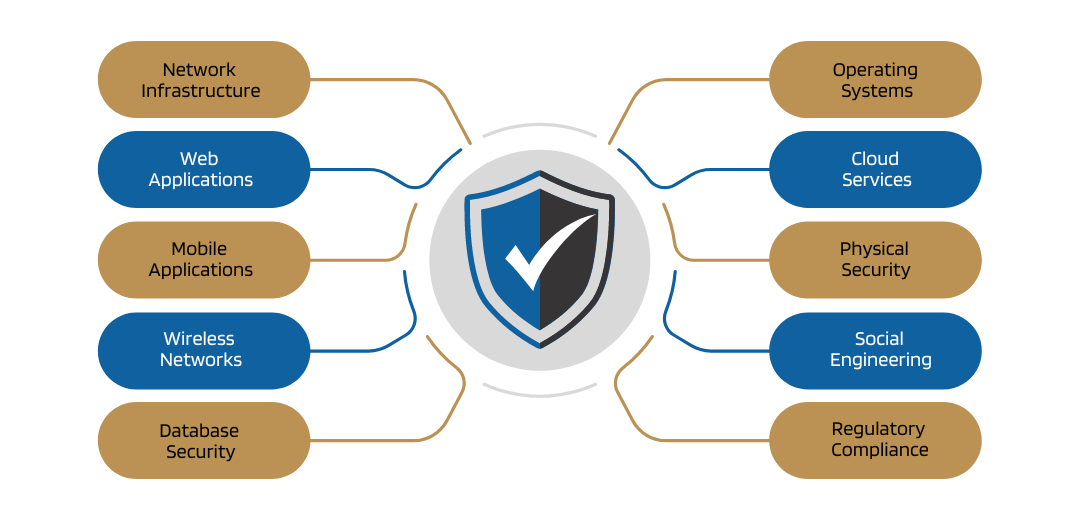
Scope in VAPT Services for Maximum Security
The scope of VAPT (Vulnerability Assessment and Penetration Testing) services is a critical element that determines the effectiveness and thoroughness of the security evaluation. Defining the scope involves identifying the assets, systems, and components to be assessed, ensuring complete coverage that aligns with your security objectives.
A well-defined scope ensures that the VAPT process is focused, efficient, and effective, addressing all critical areas of your organization’s infrastructure and operations. This thorough approach helps in identifying and mitigating risks, thereby strengthening your overall security posture.
Your Trusted VAPT Company led by Experts
As trusted VAPT experts, we are dedicated to securing your digital infrastructure through Vulnerability Assessment and Penetration Testing. With a commitment to excellence, we go beyond identifying vulnerabilities; we craft customized solutions that protect your systems from potential threats. We empower your business to navigate the complexities of cyber threats and maintain its integrity and trust.
Our Statistics
Years of Experienced Team
Pin Codes Served in India
Spam E-mail Prevented
Tech Companies Allied
CyberChef: Your Trusted Partner for Expert Cyber Security against Evolving Cyber Threats
CyberChef a Brand of Techchef Group is your trusted partner in expert cybersecurity, dedicated to protecting your valuable assets. Our comprehensive approach includes advanced vulnerability assessments, penetration testing, and continuous monitoring to identify and mitigate risks effectively.
With extensive industry experience, we offer proactive solutions customized to your unique security needs. Contact CyberChef for detailed insights, actionable recommendations, and reliable support, empowering your business to stay resilient.
Top Reasons to Choose Us for Expert Cyber Security Solutions!
Choose us for expert cyber security solutions backed by years of expertise and a commitment to protecting your valuable assets. Our dedicated team of professionals brings years of experience and industry-leading practices to every project, ensuring complete protection against cyber threats.
With a client-centric approach, we deliver customized solutions that align with your business objectives and give you confidence in your cybersecurity posture. Trust us to secure your systems with reliable, and innovative security solutions .
VAPT Security Audit Services
VAPT Assessment Company

What is CyberChef?
CyberChef is a leading cybersecurity service provider and a brand of Techchef Group specializing in providing complete security solutions, including Vulnerability Assessment and Penetration Testing (VAPT), threat intelligence, incident response, and security consulting. Our mission is to help organizations protect their digital assets and maintain a powerful security posture against evolving cyber threats.
Where are CyberChef’s offices located?
CyberChef has multiple branches to serve clients nationally. Our main office is located in Delhi, with additional branches in Mumbai, Bengaluru, Chennai, and Kolkata. Each branch is staffed with experienced cybersecurity professionals ready to assist clients with their security needs.
How does CyberChef ensure confidentiality and data privacy?
At CyberChef, we prioritize confidentiality and data privacy. We adhere to strict confidentiality agreements and implement powerful security measures to protect client information throughout our engagement. Our policies and practices comply with industry regulations and standards to ensure the highest level of data protection.
What sets CyberChef apart from other cybersecurity companies?
CyberChef stands out due to our customer-centric approach, experienced and certified team, and innovative use of advanced tools and technologies. We prioritize understanding our client's unique needs and provide tailored solutions that are both effective and sustainable. Our commitment to excellence and continuous improvement ensures that we stay ahead of emerging threats.
Quick Contact
Fill the form below and Lets talk to an Expert

Ensure the resilience of your digital infrastructure with our complete Vulnerability Assessment and Penetration Testing (VAPT) solutions. We analyze your systems to uncover vulnerabilities, employing innovative plans. Our expert team reduces attack scenarios to identify potential entry points and mitigate risks before exploiting them.
By partnering with us, you gain a proactive security approach customized to protect your data, operations, and reputation. From initial assessment to actionable insights and ongoing support, trust us to strengthen your security against cyber threats.
Get In Touch
Need trusted VAPT services in India? We’re here to help! With over 20 years of experience in Cyber Security, our team is ready to protect your digital systems. Our main office HQ is in New Delhi, and we have branches in Chennai, Mumbai, and Bengaluru for your convenience. We offer Vulnerability Assessment and Penetration Testing (VAPT) to keep your business safe and secure from cyber threats. Just fill out the form to contact us, and we’ll work together to secure your business. We’re always here for you!
MEET OUR MOST TRUSTED
Partners & Clients

"Engaging with your VAPT services was a game-changer for us. The thoroughness and professionalism of your team provided us with a clear understanding of our security weaknesses and actionable steps to address them. Now we have greater confidence in our ability to protect our customers' data and comply with regulatory requirements."

"Choosing CyberChef for VAPT was one of our best decisions. They carefully identified and resolved potential security gaps, providing actionable insights to enhance our security. Their expertise and proactive approach have been invaluable in protecting our sensitive data. We appreciate their team's expertise and responsiveness throughout the process. Thank you for your dedication to keeping our digital infrastructure secure."
OEM Alliance








....and many more.
FAQs
Common Frequently Asked Questions related to VAPT Services in India
A: The scope includes identifying which systems, applications, networks, and devices will be tested. This is typically determined based on the organization's specific security needs and objectives.
A: All industries can benefit, particularly those handling sensitive information, such as finance, healthcare, retail, and government sectors, where security and regulatory compliance are critical.
A: Yes, follow-up testing, or re-testing, is essential to verify that vulnerabilities have been successfully mitigated and no new issues have been introduced during the remediation process.
A: Types include black-box testing, white-box testing, and grey-box testing, each offering different insights and levels of thoroughness.
A. Internal VAPT focuses on vulnerabilities within the internal network, while external VAPT targets systems exposed to the internet, such as web applications and external-facing servers.
A. Vulnerabilities are prioritized based on their severity, potential impact on the organization, and likelihood of exploitation. This helps in addressing the most critical issues first.
A. The process typically includes planning and scoping, information gathering, vulnerability scanning, penetration testing, analysis and reporting, and remediation support.
A. Effectiveness can be measured by the thoroughness of the identified vulnerabilities, the relevance of the recommendations provided, and the successful implementation of remediation measures.
A. Yes, VAPT can identify weaknesses that could be exploited in an attack, providing insights that help in developing effective incident response strategies and improving overall preparedness.
A: VAPT is a critical component of a comprehensive security strategy, providing actionable insights to improve defenses, support incident response planning, and ensure ongoing security posture management.
Why Choose US
A: Our VAPT services stand out due to our use of advanced tools, experienced security professionals, and a complete approach that covers all aspects of network and application security. We also provide detailed reports and actionable recommendations to mitigate identified vulnerabilities.
A: Our team consists of certified security experts with extensive experience in the cybersecurity field. They have worked on numerous VAPT projects across various industries, ensuring a deep understanding of different security challenges and solutions.
A: We follow industry-standard methodologies, including OWASP, OSSTMM, and NIST frameworks. Our approach is thorough and systematic, ensuring that we cover all potential security threats.
A: Yes, we customize our VAPT services to meet the specific needs of each client. We understand that every organization has unique security requirements, and we design our testing strategies accordingly.
A. We plan and execute our tests with minimal disruption in mind. Our team coordinates closely with your IT staff to schedule tests during off-peak hours and ensure that critical systems remain unaffected.
A. Certainly, in previous engagements, we have identified critical vulnerabilities such as SQL injection flaws, cross-site scripting (XSS) issues, and misconfigurations in network devices. We provided detailed remediation plans that our clients successfully implemented to enhance their security posture.
A. We prioritize data confidentiality and adhere to strict non-disclosure agreements. All data collected during testing is securely stored and only accessible to authorized personnel. Our processes comply with industry best practices and regulations.
A. We provide complete reports that include an executive summary, detailed findings, risk ratings, and practical remediation steps. Our reports are designed to be clear and actionable, enabling your team to address vulnerabilities effectively.
A. We recommend conducting VAPT at least annually or whenever there are significant changes to your IT infrastructure, such as deploying new applications, updating systems, or experiencing a security incident. Regular testing helps maintain a powerful security posture.
A: We offer a range of VAPT services, including network vulnerability assessments, web application penetration testing, mobile application security testing, cloud security assessments, and social engineering tests.
Case Study: Enhancing Cybersecurity for a Financial Services Company
A leading financial services company provides a wide range of financial products, including banking, insurance, and investment services. With a substantial customer base and sensitive financial data at stake, the company prioritized strengthening its cybersecurity measures to protect against potential threats.
- Regulatory Compliance: The company needed to comply with strict financial regulations such as GDPR, PCI DSS, and SOX, which required strong security measures and regular vulnerability assessments.
- Complex IT Infrastructure: The company operated a complex IT infrastructure with multiple interconnected systems, including web applications, internal databases, and third-party services.
- Evolving Threat Environment: The financial sector is a prime target for cybercriminals, necessitating proactive measures to identify and mitigate new vulnerabilities.
The finance company engaged our VAPT services to conduct a complete assessment of their IT infrastructure. Our approach included the following phases:
- Initial Consultation and Scoping: We held a series of meetings with the company’s IT and security teams to understand their specific needs, business operations, and regulatory requirements. Together, we defined the scope of the assessment, covering external and internal networks, web applications, and critical databases.
- Inspection and information gathering: Our team conducted a thorough inspection to identify all potential attack vectors, including network mapping, open ports, and publicly available information about the company.
- Vulnerability Assessment: Using automated tools and manual techniques, we scanned the network and applications for known vulnerabilities. This included identifying outdated software, misconfigurations, and weak security controls. We performed a detailed code review of the web applications to uncover any security flaws, such as SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms.
- Penetration Testing: Our ethical hackers imitate real attack scenarios to exploit identified vulnerabilities. This step helped us understand the potential impact of each vulnerability and the ease of exploitation. We tested both external and internal systems to ensure complete coverage.
- Reporting and Remediation: We provided a detailed report outlining all discovered vulnerabilities, their risk levels, and their potential impact on the business. The report included clear, actionable recommendations for remediation, prioritized based on the severity of the vulnerabilities.
- Post-Engagement Support: After delivering the report, we worked closely with the company’s IT team to assist in implementing the recommended fixes. We conducted follow-up testing to verify that the vulnerabilities had been successfully remediated and that no new issues had arisen.
- Improved Security Posture: The company significantly enhanced its security posture by addressing critical vulnerabilities identified during the VAPT engagement. This included patching software, reconfiguring network devices, and improving application security practices.
- Regulatory Compliance: The company achieved compliance with relevant financial regulations, reducing the risk of legal penalties and improving customer trust.
- Risk Reduction: By proactively identifying and mitigating vulnerabilities, the company reduced the risk of data breaches and cyberattacks, protected sensitive customer information, and maintained business continuity.
- Enhanced Awareness: The engagement raised awareness within the company about potential security threats and the importance of regular security assessments.
This case study demonstrates the effectiveness of our VAPT services in enhancing the security posture of a financial services company. By identifying and addressing vulnerabilities, the company was able to protect sensitive data, comply with regulations, and reduce the risk of cyber threats.



